PETALING JAYA: The risks are high, yet the safety measures are inadequate about sums up the state of cyber-security in Malaysia.
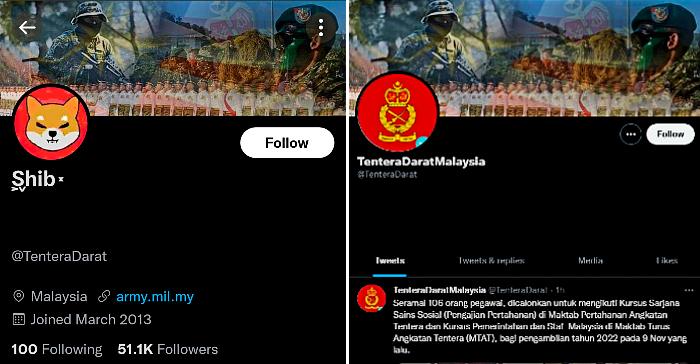
Coupled with the loss of sensitive information that could have an impact on national security, there is also the possibility that misinformation is disseminated without the government even realising it, according to experts in the field. The Nov 11 hacking of a Malaysian army Twitter account is a case in point.
According to Dr Selvakumar Manickam, an associate professor at Universiti Sains Malaysia and an expert in the field, at times it could come down to just a simple case of poor password practice.
“The habit of using easy to remember passwords for official government emails, social media accounts, and even critical government servers seems to be quite prevalent,” he told theSun.
He said the government should introduce policies to require strong passwords and frequent changes of passwords should be mandatory. “Such accounts should also be managed only by those well educated in this and related fields,” he said.
Cyber-security expert and criminologist Shankar Durairaja noted that in Malaysia, there are no comprehensive standalone cyber-security laws but there are several, such as the Computer Crimes Act 1997, the Communications and Multimedia Act 1998 and Personal Data Protection Act 2010 (PDPA) that address the issue.
“However, many of these laws have not been revised or amended (to meet current requirements),” he told theSun.
For instance, he said, the PDPA only bars inappropriate use of personal data for commercial purposes but does not cover breaches involving online communities.
On Nov 11, the suspicion of netizens was aroused by a change in the name of the army’s Twitter account to “Shib” and the profile picture replaced by an image of a dog named Shiba Inu, which is also a cryptocurrency logo. The account was secured 24 hours later.
Selvakumar said the greatest threat posed by continued hacking of government websites is data theft, especially personal information of users such as addresses, identification numbers, phone numbers, and emails.
“This data could be sold on the dark net for a handsome amount, which other criminals buy to carry out phishing attacks or online scams,” he said.
Shankar noted that governmental accounts are often targets of hackers because they consist of highly sensitive information that can be sold or used for marketing, fraud and identity theft for huge financial rewards.
The significance of such failures is huge. Apart from damage to reputation and operations, people could lose confidence, leading to political instability, financial losses and loss of investor confidence.
“Government bodies must train network engineers and system administrators in security-related skills to manage and configure systems securely. Besides that, they should consider hiring cyber-security experts to stress-test the government systems to identify weaknesses and vulnerabilities and remedy them,” Shankar said.
Cyber-security testing firm LGMS group chief executive officer Fong Choong-Fook offered a scarier scenario.
“Imagine hackers getting into a government account or website, maintain the site and then publish misleading information while masquerading as the government,” Fong told theSun.
“This is scary because people may be misinformed and the government may not even know this,” he said.
Fong added that this is not a one-off situation or something that can be regarded as a “what if” situation.
Instead, he noted that hackers are constantly making attempts to hack into government sites.
“Nowadays, cyber-security experts are advocating a new concept called a compromise assessment which is used to assess whether an organisation has been compromised or not.
“This way we will be aware if our sites or accounts have been breached. I also believe that the government needs to be more aggressive to hunt down these cyber threat individuals,” he added.