INTERNET fraud involves using services or software with internet access to attempt to defraud or take advantage of victims. It encompasses cyber-criminal activities including identity theft, phishing and other social engineering activities designed to scam people of their personal information. These scams will target victims through fraudulent activities that rob people of their money. And the figures we observe continue to increase as internet usage expands and cybercrime techniques become more sophisticated.
Types of internet fraud
A variety of strategies is used to commit internet fraud. It includes activities done through malicious software, email and instant messaging services to spread malware and links to spoofed websites that steal user data, along with wide-reaching phishing scams.
Internet fraud can be broken down into several types including:
Phishing and spoofing: The use of email and online messaging services to convince victims into sharing personal data, login credentials and financial details.
Data breach: Stealing confidential, protected or sensitive data from a secure location and moving it into an untrusted environment, which also consists of data being stolen from users and organisations.
Denial of service: Disrupting the traffic to an online service, system or network with malicious intent.
Malware: The use of malicious software that damages or disables a user’s device or steal personal and sensitive data.
Ransomware: A malware that prevents users from accessing critical data, then demanding payment to restore access. Ransomware is typically delivered via phishing attacks.
Business email compromise: A sophisticated attack that targets businesses that operates on wire payments. It compromises legitimate email accounts through social engineering techniques to submit unauthorised payments.
To avoid hackers’ internet fraud attempts, users need to understand the common examples of internet fraud and tactics:
Email phishing scams
Email-based phishing scams are among the most prevalent types of internet fraud, which continues to pose a threat to internet users and businesses.
Statistics from Security Boulevard show that in 2020, 22% of all data breaches involved a phishing attack, and 95% of all attacks that targeted business networks caused by spear phishing. Furthermore, 97% of users could not detect sophisticated phishing email.
About 1.5 million new phishing sites are created every month, and 78% of users understand the risk of hyperlinks in emails but click them anyway.
Email-based phishing scams constantly evolve, and it ranges from simple attacks to more complex threats that target specific individuals.
Cyber criminals in email phishing scams mask themselves as individuals that their victim knows or would consider reputable. The attack aims to encourage people to click on a link that leads to a malicious or spoofed website, designed to look like a legitimate website or to open an attachment that contains malicious content.
The hacker first compromises a legitimate website or creates a fake website and then acquires a list of email addresses to target and distribute an email message that aims to dupe people into clicking on a link to that website.
When a victim clicks the link, they are taken to the website which will either request a username and password or automatically download malware onto their device that steals sensitive information. The hacker can use this data to access a user’s online account, steal more data like credit card details and access corporate networks attached to the device or commit wider identity fraud.
Email phishing scammers will often express the need for urgency from their victims. This includes telling them that their online account or credit card is at risk, and they need to log in immediately to rectify the issue.
Greeting card scams
Many internet fraud attacks focus on popular events to scam people that celebrate them. This includes birthdays and festive occasions that are commonly marked by sharing greeting cards with friends and family members via social media. Hackers typically exploit this by installing malicious software within the greeting card, which is automatically downloaded into the recipient’s device when they open the card.
The consequences can be devastating. The malware takes the form of annoying pop-up advertisement that affects an application’s performance on a smart device.
The more worrying outcome would be the victim’s personal and financial data being stolen and their computer being compromised as a bot within a vast network of computers, also known as “botnet”.
Credit card scams
This typically occurs when hackers fraudulently acquire people’s credit or debit card details to steal money or make purchases.
To obtain these details, fraudsters often use credit card features that are “too good to be true” or through bank loan deals to lure victims.
For example, a victim may receive a message from their bank telling them they are eligible for a special loan or a vast amount of money that has been loaned to them. These activities continue to trick people despite the widespread awareness about suspicious offerings.
Online dating scams
Another typical example of internet fraud targets the variety of online dating applications and websites. Hackers focus on these apps to lure victims into sending money and sharing personal data with new love interests. Scammers typically create fake profiles to interact with users, develop a relationship that slowly builds trust. A phony story is then created and the attacker requests financial help from the user.
Lottery fee fraud
Another common form of internet fraud is email scams that tell victims they have won the lottery. These scams will inform recipients that they can only claim their prize after they have paid a small fee. Lottery fee fraudsters typically craft emails to look and sound believable, which result in many falling for the scam. The scam targets people’s dreams of winning massive amounts of money, even though they may have never purchased a lottery ticket. Furthermore, no legitimate lottery scheme will ask winners to pay to claim their prize.
The “Nigerian Prince”
A classic internet fraud tactic, the “Nigerian Prince” scam, remains common and thriving despite widespread awareness. The scam uses a premise of a wealthy Nigerian family or individual who wants to share their wealth in return for assistance in accessing their inheritance. They use phishing tactics to send emails that outlines an emotional backstory, luring victims into a promise of significant financial reward. The scam typically begins by asking for a small fee to help with legal processes and paperwork, with the promise of a large sum of money further down the line.
The scammer will inevitably ask for more extensive fees to cover further administration tasks and transaction costs supported by legitimate-looking confirmation documents. However, the promised return on investment does not arrive.
Macau scam
These fraudsters pretend to be calling from Malaysian law enforcement agencies such as the police, Inland Revenue Board, Malaysian Communications and Multimedia Commission, Malaysian Anti-Corruption Commission, with the latest being from POS Malaysia’s express delivery service Poslaju.
It starts off with a call to the victims, convincing them they have committed a crime. Hence, the victim will give out their bank user identification and password out of fear, and on many occasions releasing the TAC (Transaction Authorisation Code) to these criminals. Once this financial information is released, the victim’s savings are withdrawn through cash advances through an ATM or transferred to a mule account.
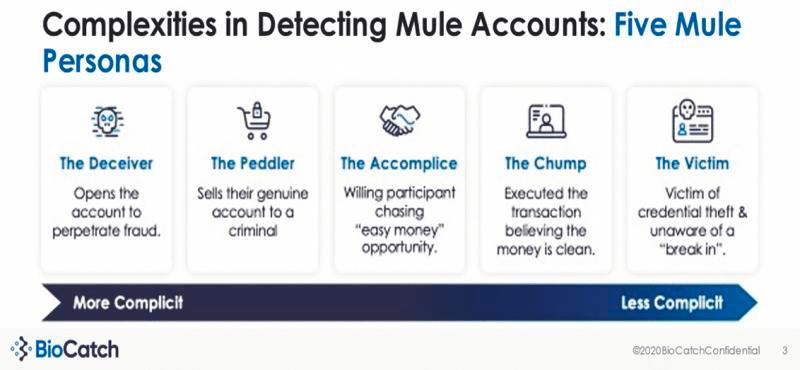
Decrypting mule account holders
A mule account is an account that belongs to an individual or company that allows it to be controlled and used by criminals. The ATM card’s PIN number or access to online banking credentials are given to these criminals who will then receive money from fraudulent activities. These mules are offered RM1,000 per week for the rental of the account. Mule account holders can be charged under Section 424 of the Penal Code for fraudulently concealing money, which carries a sentence of up to five years imprisonment or a fine, or both upon conviction, even if such mule account holders are not directly involved in whatever the “renter” does.
Android application packages (APK)
Do not download any links from unrecognised websites, social media networks that comprise of links that probably have APK files hiding to hack your smartphones. These links contain malwares, ransomware or other less visible viruses that can potentially disrupt an android operating system on your smartphones.
Methods of hacking android operating systems
1. Generating a malicious payload with “msfvenom” and extracting it as an APK file.
2. Injecting malicious payloads on legitimate android apps with “msfvenom”.
3. Both methods will either require access to the victim’s phone or some form of social engineering on the attacker’s part to get their victims to install the malicious APKs on their phones.
Preventing online attack
1. Ensure “Install from unknown sources” is disabled in your phone settings.
2. If possible, only download apps from Google Play Store (much safer than downloading from third party sources).
3. Install anti-virus on your smartphones to scan for malicious apps.
4. Review the permissions an app is asking for. If they seem too much, be on your guard (e.g. a flashlight app asking for access to your contacts, SMS, microphone, etc).
5. Carefully review links you have been sent (beware of misspelled names or “free promotions”).
6. When installing an app from unknown sources, Google Play Protect always requests to scan it. Allow it to do so.
Protecting users from internet scams
Internet users can protect themselves and avoid being caught in a phishing line by remaining vigilant of the common types of internet fraud listed above. It is vital to never send money to someone met over the internet, never share personal or financial details with individuals who are not legitimate or trustworthy. Never click on hyperlinks or attachments in emails or instant messages. Once targeted, internet users should report online scammer activity and phishing emails to the authorities.
For every unknown transfer, it is better to verify accounts on the police “semak” mule website: https://semakmule.rmp.gov.my.
Credit card fraud can also be avoided by keeping a close eye on bank accounts, setting up notifications on credit card activity, signing up for credit monitoring and using consumer protection services. If users suffer credit card fraud, they must report it to the relevant legal authorities and credit bureaus.
Comments: letters@thesundaily.com